This is Part 10.
Here is a post from a friend of mine:
5 names everyone should know in the age of Biodigital Convergence are Ian F Akyildiz, Francois Coallier, MC-ROCO, Charles Lieber & Kristel Van Der Elst.
There’s many more names but those people should be in your vocabulary.
__________
4IR for pets:

__________________
Here is a post shared by a friend of mine:
Internet of Everything (IoE) – From Molecules to the Universe Murat Kuscu https://www.researchgate.net/publication/370617728_Internet_of_Everything_IoE_-_From_Molecules_to_the_Universe
_____________
_____________
Here is a post from a friend of mine:
This post is my attempt to expose and clarify the lies and deception that is being sold to the world regarding blockchain, smart-contracts, DAOs, Web3 and AI governance. There is a lot of information in this post so grab your coffee, tea or favorite beverage.
The media gives the impression that blockchain-based decentralization is a good thing and that allowing an AI-controlled Decentralized Autonomous Organization (DAO) system to govern human affairs, on a global scale, would be very beneficial to us. Perhaps IF we lived in a world run by honest players, MAYBE this would be true, but in the REAL WORLD we are governed by very rich, very powerful, very greedy and very narcissistic dishonest players, and where there is unbounded power, you will find endless lies and deception. This new world order of “decentralization” is no different.
Before we proceed, I have to first give a short description of what blockchain, smart-contracts and decentralization is, and then lead into DAO and its false and dangerous promise of governing (the globe) using AI.
Table of contents:
Bitcoin and Blockchain
Ethereum and Smart-Contracts
Decentralization
Brief History of Digital Decentralization
Consensus and Voting
Distributed Autonomous Organization (DAO)
The Risks and Dangers of DAO
SingularityNET
List of SingularityNET AI “Services” Organizations
AI-DSL: General-Purpose Language for AI Agents
SophiaDAO: The Merging of All AIs
AI Governance Within UN SDG, ESG, CBDC and Web3
The Corrupt Global AI-Governance Machine (The Beast)
Here is a post from another friend of mine:
Welcome to the future of Amerika , the end of privacy
CHINA Subway system passengers must scan their face or hand in order to ride, powered by WeChat, China’s “everything app.”
If they have been blacklisted from China’s social credit system, the doors won’t open.

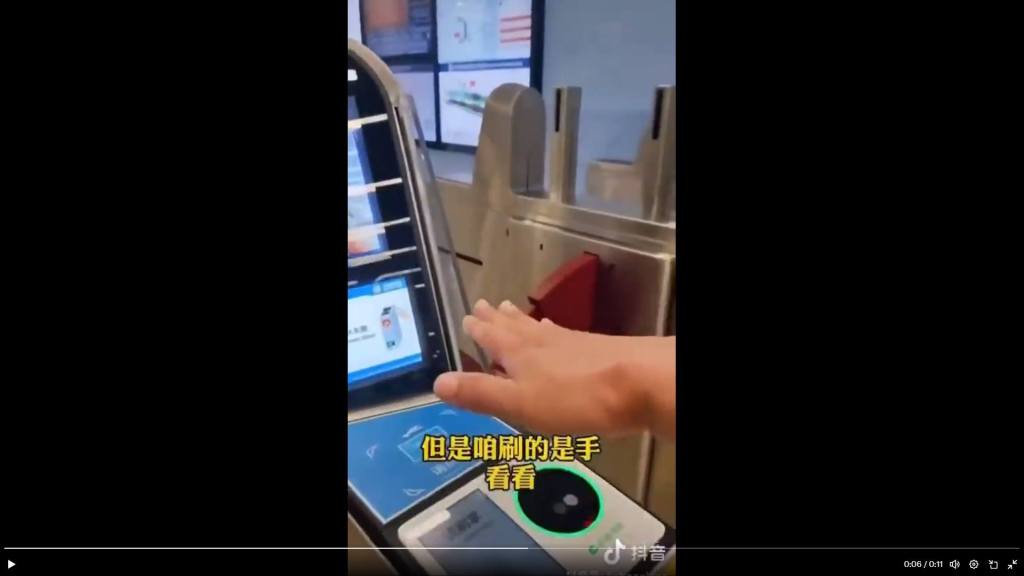
____________
Here is a post from my friend from Tulsa:
The following press release from #Oklahoma#State#Representative#Tom#Gann has incurred the ire of those who wish to measure, manage, and monetize the people of Oklahoma.
Please help circulate this important information to Oklahomans across the state.
I added the attached screenshots.
State Representative: #Warrantless#License#Plate#Scanner#Tracking is Not Authorized By State Law
State Representative Tom Gann issued a statement today following the dramatic defeat of SB 1620 on Thursday.
“In 2016, the legislature made the unfortunate decision to authorize the use of license plate scanner technology for the purpose of insurance verification. That law limited the use of this #intrusive#technology to that purpose only. This year, the legislature considered House Bill 3570, which was not heard prior to the 3rd reading deadline, and Senate Bill 1620, which was defeated on Thursday by a wide margin — becoming one of the very few bills to be defeated on the Senate floor. These bills would have authorized the use of this technology for purposes other than insurance verification. As these laws have failed, it’s important for the public and city councils across the state to know that: There is #no#specific#statutory#authorization for using these systems.”
While the legislature was considering these proposals, Gann says that numerous concerning details have been brought forward.
While the advocates of this data advocate for its ability to automate NCIC and Amber alert scanning, it’s clear that the real impact of this technology is to create a #database of #vehicles‘ #travels, complete with the vehicles’ identifiers, including its bumper stickers, and to then allow warrantless searches of that data, data that’s stored in the cloud and that is then subsequently shared with many, many diverse government entities including those that are not in Oklahoma.
To demonstrate this concern, Gann pointed to the fact that in the past 30 days, #Tulsa‘s #data#collection has been queried 2,143 times compared to 1,364 Amber and NCIC alerts.
“That’s 2,143 searches that have clearly occurred without a warrant and undoubtedly compromised the information of many innocent persons,” Gann states.
Gann also states that departments who use this technology have been known to share access to the data collection with federal agencies, including the FBI and ATF.
“No Oklahoman should ever have to worry about their movements being shared with the Biden Administration’s federal police state,” Gann declared. “That’s clearly what this technology is enabling.”
In the case of the Del City Police Department, that Department appears to be sharing their information with more than 60 other government entities including the US Postal Service, the Kansas Bureau of Investigation, and the Texas Financial Crimes Intelligence Center.
In addition to sharing Oklahomans’ travel data with many government entities, the technology also appears to allow government entities to create custom hit lists that will inform them whenever certain people attempt to travel into or within their city limits.
“In my view, these abuses are clear violations of the 4th Amendment, and are not specifically authorized by state law. By defeating SB 1620 by such a wide margin, the Legislature has clearly signaled that it doesn’t intend to authorize them at any point in the near future.”
Tulsa: https://archive.is/SMyNY
Del City: https://archive.is/Jcq7e
_______
____________
_____________
Here is a post from a friend of mine:
Please study and share this website on the Biodigital Convergence and Smart Cities I put together- it’s loaded with information to empower! ![]()
_________________
And another post from him:
We all have nanotechnology inside us right now that can alter our genome and interface with our surroundings without our permission- this is the Biodigital Convergence:
Bi Fi
Biological Internet and communication between Hosts through a biological communication network embedded in human bodies.
The idea of the Biological Internet is to stay forever active (while alive) in human bodies, using kinetic, thermal and any other energy that our bodies constantly generate and through the integrated biosensors, metamaterials and liquid nanotechnology to transmit and transmit information, signal. To turn off the Biological Internet, it’s not enough for the power to go down or 5G towers, or any other part of mobile networks, but just die.
That is, there is no exception in life!
This is what they are building now and this is what they are hiding to be able to implement in all of us the necessary components that generate a signal, fed by the tissues, the heart, the blood flow, our erythrocytes, and then when a fact is done, they may announce publicly our digital, bio-synthetic implementation into the global information system of mega AI and the neural network through which it has been created.
Biosensors, as metamaterials and nanotech, enter human bodies and INSIDE are assembled, using in addition to synthetic components and biological ones, so that they can be so well absorbed into the tissues, organs, bone marrow, brain and DNA itself that they cannot be cleared by the Immune System, and The Immune System itself has undertaken to replace it with a Digital, digital, controlled and acting by someone’s remote commands.
I write this not to despair you, but to aspire you to stop accepting nanotechnology in the form of injections – vaccines of any kind! Stop ingesting garbage, from those we have a choice to stop ingesting because aerosols getting into water and food we cannot avoid. Then seek for detoxification of the body personally and until the network inside you that will connect you to the Bi Fi network is built, do not allow at least your existing components to be upgraded.
What decomposes technology, what decomposes micelles, fungus, what decompose parasites they use as biological carrier of synthetic components?
Think you might have better ideas than I do.
Use massively all means, smartly and adapted to your own physique. There are no magic pills, no rescuers to draw them for you, no universal protocol! Start thinking with your heads and don’t wait, there is no time. For example, salt breaks down chips, you choose how and in what way you will use it. Good fat helps cells not burn out, conditionally speaking. Garlic, the good natural apple vinegar, antifungal herbs, antiparasitic herbs (look for them yourself which ones are and which ones suit you), as well as other biological remedies, are our helpers. Avoid medications and supplements supposedly detox, all pharmaceuticals are compromised.
If the Biological Internet is built, even if it cuts off the power, even if there is a solar flare to ruin the built infrastructure of 5, 6 etc. in the G system, our bodies, if watered and with assembled nanorouters, metamaterials and biosensors, will emit and receive a signal! So those holding our digital doppelgängers in IBM’s mega quantum underground computer powered by renewable, free energy will continue remote monitoring and control, so let mankind go wild again, having lost electricity and civilized amenities.
Did you understand the seriousness of what I’m warning you about?
And yes, this has already happened, but who can understand what lies behind the murals and petroglyphs? Those who carved them left the only possible information for future generations to warn them, we are dumb enough first not to pay attention to them and secondly unable to read and interpret them.
Start listening to your sixth sense before it is replaced with kosher thinking. There are no ready-made recipes.
In the emerging nano-bio-info-cognitive-AI (NBICA) society, we become the batteries. Our bodily fluids will be harvested via graphene-enabled superconducting ink & connected to Bluetooth to power the advancing Smart grid and Smart cities (IoT+IoB+IoBNT):
The Capability To Wirelessly Edit Your Genome
Your cells are the same as computing components, and they can be upgraded to enhance these functions and new ones.
And once this “system” is installed, they can wirelessly edit your genome and do all kinds of things….
The molecules that are emitted by genetically modified bacteria and cells, inside the human body, are converted and read into Binary Machine Code of 1s and 0s, to inside and outside networks.
“It greatly depends upon who controls these technologies and make the choices.”
Prof. Josep Jornet
He is the star student to Prof. Ian Fuat Akyildiz
He also designed the “Plasmonic Antennas” technology for the bloodstream.
The CIA held the patent on it, until 2017 when it was released, per Prof. Akyildiz
In simple terms – Wirelessly…
Essentially, it is the new wireless and remotely accessed Healthcare solution for everyone.
Processed by AI machine learning.
It is a symbiotic relationship.
Nano technology in use inside humans and animals consists of:
1. Engineered Bacteria, primarily e. COLI
2. Genetically modified cells and proteins.
3. Man made, self assembling components using G.O. and hybrids that combine both man made and biological elements.
Your cells and bacteria have the same functionality as lets say computer components, but through “engineering”, they are enhanced.
Your body is way more advanced then you might realize.
Molecular Communications means that the bacteria and cells use released molecules to talk to each other.
Plasmonic antennas are placed into the blood stream.
Bacteria, cells and proteins are targetable, meaning they can be directed where to go but as you imagine, they travel slowly.
Lipid nano particles or LPN’s are vehicles or trojan horses, that bypass the normal immune system responce, to deliver different payloads.
Hydras were also found to be true, and experimented with through a video produced by the Tel Aviv University and German researchers.
How widespread these hydras are or what current uses are unknown to me. In the video, the goal was for regeneration of body parts etc.
There are many countries around the world who have been developing their own “systems”, with and without cooperation with other nations and research teams.
IoBNT or “The Internet Of BioNano Things” has been in development since 2004.
The full weight of the American government, was put behind bringing nano tech to the world in such ways, starting in 2002.
This installed system, through injections etc, uses Bluetooth, NFC or near field communications, molecular communications, LiFi, Optical light based, etc to access the internet.
The development and deployment of IPv6 addresses coincides with Agenda 21 & IoBNT.
Edit:
Nov. 2nd, 2023
Pete Ramón writes:
Plasmonic antennas aren’t limited to graphene oxide, they can also be made from metals such as gold, silver, titanium dioxide, iron oxide and other oxides.
Many oxides are used as food additives, especially TiO2, ZnO, SiO2, and red, yellow, and black iron oxides.
Gold nanorods have found use as plasmonic aerosols.
And as we all know by now, silver is used for cloud seeding.
All these nanoparticles finding their way into the environment, into plants, animals, and us.
Detoxing methods will work easily for some materials, while others may be harder to remove or not able to be removed at all, like carbon nanotubes and asbestos fibers.
E. Coli is the main engineered bacteria used in IoBNT – The Internet of BioNano Things.
There are also genetically modified cells, inserted proteins that binds to the brains neurons for light/optical brain interface in regards to blue light “Optogenetics” and man-made nano machinery that self assembles. And “hybrids”.
The protein “trick” is way more advanced then “Neurolink”, which is old technology….Does not require surgery or holes in your skull.
“Lentivirus cell” ( a special type of virus used in genetic engineering) to infect and insert new DNA code into human cells and reprogram the DNA or insert new DNA or parts of DNA of other human cells.
The long-term goal is to infect and insert new DNA code into human cells and reprogram the DNA or insert new DNA or parts of DNA of other human cells.
Luciferase is used to show if your infected or not with the virus etc….
Upon detection of infection or disease, the system releases bioluminescence or florescence.
Can be used for other detections and or signaling.
The system uses, bluetooth, Near Field Communications, Molecular communications and LiFi – light/optical.
Wirelessly…
Now, after read the post, look up “Optogenetics” on my page and elsewhere.
Human and Animal Drones since 2009.
1 tiny protein installed to your neurons….
Dr. Charles Morgan – Neuroscientist – West Point Academy Lecture 2018
Canadian government website.
https://horizons.service.canada.ca/en/2020/02/11/exploring-biodigital-convergence/index.shtml
https://horizons.service.canada.ca/en/2022/05/31/biodigital-today-and-tomorrow/
- Standards Council of Canada.
https://www.scc.ca/en/news-events/news/2021/canada-forefront-exploring-biodigital-convergence
US:
https://www.nsf.gov/crssprgm/nano//reports/NNI-at-20-years_JNR-2023-PREPRINT-(MC-Roco)-2.pdf
https://www.nsf.gov/crssprgm/nano/reports/NNI_17-0817_Progress%20In%20Convergence-Basic%20Concepts%20and%20Applications_%40MexicoCity_MC%20Roco_45min_web.pdf
Europe:
Over 500pgs on Wireless Sensor Networks from Ian F Akyildiz for the Nano-Bio-Info-Cogno/Biodigital Convergence experiment.
Our military is using SMART dust for both environmental & health monitoring.
https://www.academia.edu/26537390/_IAN_F_AKYILDIZ_SERIES_IN_COMMUNICATIONS_AND_NETWORKING
https://www.nanowerk.com/smartdust.php
Battelle-Led Teams wins DARPA award to develop an injectable Bi-directional Brain Machine Interface.
Battelle is one of the core organizations working with the military Industrial complex integrating biotech & neurotechnology= Bioelectronics.
https://www.battelle.org/markets/health/medical-technology/neurotechnology
They also work on advanced materials, semiconductors, nanomaterials, etc.
https://www.battelle.org/expertise/advanced-materials
Battelle to explore artificial intelligence neural interfaces with DARPA award.
Some more Battelle Expertise in the Military Industrial Mind Control Program.
https://www.battelle.org/expertise
Battelle also work with cellular nanomedicine for a NON-INVASIVE, NON-SURGICAL, BRAIN MACHINE INTERFACE.
http://cellularnanomed.com/
Cellular nanomedicine: Patents and Publications. http://cellularnanomed.com/patents-publications/
DREADDS & CRISPR
Psycho-Neurobiology and War – Dr. Charles Morgan
West Point Academy Lecture
They can add and subtract anything to the DNA and it can be done remotely via the right signal. Allows for human and non-human animal drones and augmenting humans as needed for missions in military & security as examples.
(((“Perhaps even in real-time usage”. My own words…)))
DREADDS can be remotely controlled and activated when the body is exposed to the right “signal” or frequency…
Transfer memory. Create any product as long as you know the correct DNA sequence and insert it into a living organism. And you can remotely control it. Affect the way you think and act.
“Gene Doping” was preemptively banned for athletes by the World Anti-Doping Agency, and this has been feasible since 2013.
https://youtu.be/FAnM9XhUdio
The Full Video Lecture Here:
Video 56 mins
Dr. Charles Morgan on Psycho-Neurobiology and War
Dr. Charles Morgan speaks to cadets and faculty at West Point about a range of topics, including psychology, neurobiology, and the science of humans at war. Dr. Morgan’s neurobiological and forensic research has established him as an international expert in post-traumatic stress disorder, eyewitness memory, and human performance under conditions of high stress.
The event was organized and hosted by the Modern War Institute at West Point.
https://youtu.be/cTtIPBPSv0U
World Anti-Doping Agency
https://www.wada-ama.org/en
All prohibited methods in this class are non-Specified except methods in M2.2. which are Specified Methods.
The following, with the potential to enhance sport performance, are prohibited:
- The use of nucleic acids or nucleic acid analogues that may alter genome sequences and/ or alter gene expression by any mechanism. This includes but is not limited to gene editing, gene silencing and gene transfer technologies.
- The use of normal or genetically modified cells.
See M3 “Gene And Cell Doping” Prohibited List
DREADDS
https://www.wada-ama.org/en/prohibited-list
DREADDS For Neuroscientists – Search Results
https://duckduckgo.com/?q=dreadds%20for%20neuroscientists…
Dr. Charles Morgan on Psycho-Neurobiology and War: CRISPR, technique used to make the Covid Vaccines
YOUTUBE.COM
Dr. Charles Morgan on Psycho-Neurobiology and War: CRISPR, technique used to make the Covid Vaccines
Dr. Charles Morgan on Psycho-Neurobiology and War: CRISPR, technique used to make the Covid Vaccines
The international standards from the IEC regarding biodigital convergence are responsible for worldwide standardization surrounding Biodigital Convergence in over 170 countries.
https://www.iec.ch/system/files/2023-10/wsdcombinedpdf_0.pdf
Graphene Antennas/Communications In Human Bodies – Part One
Communication devices used in the human blood vessels, as of Sept. 2020.
And
“Intelligent Communication Environments” which comes from 6g networks for real-time sensing and mapping of environments (plus tracking the humans…of course.)
Video Clip 29 mins 21 secs
Internet of BioNano Things – Part 47
Graphene Based Plasmonic Nano-Antennas Used In IoBNT, Installed Inside Human Bodies, For Communications.
US Patent No. 9,643,841 issued on May 9th, 2017.
The professor says they applied for this patent but the CIA did not allow it until the CIA released in 2017…
Terrahertz band plasmonic nano-transceiver
For wireless communications in the THz band.
US Patent No. 9,397,758 issued on July 19th, 2016.
Zinc Oxide Nanowires can be used fr vibrational energy harvesting systems in nano devices used for IoBNTT.
Uses the pulse of your heartbeat and the flow of your blood through your vessels to supply this.
Called Piezoelectric nano-generators.
DNA stores data, gathered etc.
125 atoms per bit
DNA uses 32 atoms per bit.
You can have “many” terabytes worth of information stored into your DNA.
Gold nanoparticles for memories is also mentioned here.
He asks if they should be using IPv6 IP addresses for the system…
Talks about maybe using lower frequencies and the materials needed for it.
He says graphene is “the first of a kind” but not the only one…
Molybdenum + sulphur (MoS2)
Hexagonal Boron Nitride (h-BN)
Combines very well with graphene, he says.
Also metamaterials.
Says they can create hybrids that combine these materials for whatever is needed.
Only the beginning he says.
He says that they are building these “Intelligent Communication Environments” (ICE) to greatly extend the ability to connect and communicate not only with IoBNT installed into people but also all of the other things that connect to the IoT – Internet of Things.
ICE will come into play under 6g sensing networks. (real-time mapping of environments with wifi)
Full Source Video Link:
In this video, only Turkish is spoken up to the 2 minute 7 sec mark
1,119 views Sep 18, 2020 – Video 1 hour 21 mins
Webinar by Prof. Dr. Ian Fuat Akyildiz.
Title: 6G and Beyond: The Future of Wireless Communications Systems
Date: 17 / 09 / 2020
Moderator: Tuğrul Çavdar, Department of Computer Engineering, Karadeŋiz Technical University, Trabzon, Türkiye
https://youtu.be/lVTeRb2JNtI
Webinar: Prof. Dr. İlhan Fuat Akyıldız: 6G and Beyond: The Future of Wireless Communications Systems
YOUTUBE.COM
Webinar: Prof. Dr. İlhan Fuat Akyıldız: 6G and Beyond: The Future of Wireless Communications Systems
Webinar: Prof. Dr. İlhan Fuat Akyıldız: 6G and Beyond: The Future of Wireless Communications Systems
2w
Reply
Love Billy
H/T Brian Mitchell
Prof. Ian Fuat Akyildiz had a vision that became reality….
To create a real-time, biological-digital interface.
Connecting all of us, to the digital world.
The future of wireless communications is to create a real-time biological interface for both humans and the animals.
The introduction of graphene nano antennas and materials in 2004, is how the “Internet of Bio Nano Things” started, and became a reality.
The research began in 2004.
This effort began in earnest in 2009 with Dr. Ian Akyildiz. Prof. Jornet is his star student.
The term “Internet of Bio Nano Things” was thought of by Prof. Ian Fuat Akyildiz in 2008, at about 3am in the morning, one night.
It was brought to the world in 2020 and the wildfire caught, in 2021…
“It was way sooner then that in many other places in the world…
You just, do not know it yet, but you will….
Not only is IoBNT an interface, but it is also a 1st generation, Bio-Cyber defense platform, for the human body, complete with anti-virus…
Why?
Because the present and future of warfare will be at the biological nano scale, and the knowledge to hack human beings is wide-spread now, across the world.
Individuals, organizations, groups, and entire nations are actively fielding such weaponry and abilities.”
All the Standards surrounding Biodigital Convergence run on digital twin technology, blockchain/ WEB3, Internet of Things, & SMART City standards.
All of these technologies are already operable.
It’s the SMART Cities infrastructure that must be destroyed to stop WEB4 & the Fifth Industrial Revolution.
The Fourth Industrial Revolution is old news.
According to the science, all the “useless eaters ” are being force-fed nano-biosensors through the Internet of Ingestible Things.
Your SMART phone is monitoring these sensors.
https://www.ucl.ac.uk/healthcare-engineering/events/2021/mar/internet-ingestible-things-future-crime
Biodigital Convergence is the merging of biological systems with digital technology. This not only includes humans but every single biological entity. Biodigital Convergence/Nano-Bio-Info-Cogno includes many different sciences, mostly being nanotechnology, from synthetic biology, to organ on a chip, to digital twins, to nutrigenomics, plant bioelectronics, to worldwide geo-engineering experiments, etc. They’re ALL HUMAN AUGMENTATION TECHNOLOGIES.
There’s several organizations and select individuals at the top of the chain of biodigital convergence. The organizations at a standards level are the IEC, IEEE, ISO, ITU. The people with the most influence in those organizations are Francois Coallier, Ian F Akyildiz and his star student Josef Jornet. There’s also organizations like NASA, DARPA, UN, FDA, Policy Horizons, Horizons EU, Israeli Innovative Authority, IMF, Graphene Flagship, and the entire military industrial complex. Kristel Van Der Elst from Policy Horizons is one of the main influencers too.
The list is too long to mention but it’s the standardization organizations and some of the think tanks like Policy Horizons that explain the science correctly. These standardization groups have different names for the actual science. While IEC and Policy Horizons call it the biodigital convergence, IEEE call it Internet of Bodies, Internet of Bio-Nano Things, Internet of Multimedia Things, and WBAN/ BBN. The US Government seem to call it Nano-Bio-Info-Cogno/NBIC and admit it’s been going on for over 20 years.
These links may help people get a better understanding.
1.This was written by the Whitehouse in 2002. Converging Technologies for Improving Human Performance
- This progress report was written in 2017 and shows all political parties have been funding this since Clinton.
Progress in Convergence: Basic Concepts and Applications.
Here is a post from a friend of mine:
Web 7.0 DIDComm Agent Architecture Reference Model (DIDComm-ARM) 0.27
[name redacted] I’m not sure what is significant.
And a reply to this post:
Basically, your digital twin in a decentralized web will grant you access to services if you are identified and allowed.
Here is a post from a friend of mine:
Even the dollar stores in my area have AI biometric camera screens installed as you go in and the green and red boxes lit up around each person as they come in.
Do they even know what it means ?
They are not the only stores.
There’s not many so it is impactful.
________________
Here is a post from a friend of mine:
Revealed: a California city is training AI to spot homeless encampments
https://www.theguardian.com/technology/2024/mar/25/san-jose-homelessness-ai-detection
Here is a post from a friend of mine from Canada:
In my well educated opinion, the truckers Convoy was really a crowdsourcing initiative to bring in WEB3 governance into the SMART Cities infrastructure. This is why you saw the truckers use crowdsourcing platforms like Go Fund Me even though the platform froze/seized the first million dollars donated. The ones at the top continued to ask people to support the initiative even though they couldn’t access the $$. Once people wised up, they used other crowdsourcing platforms where the $$ was eventually frozen/seized too. You then saw bank accounts frozen. The reason bank accounts were frozen was to solicit everyday people to support using Crypto. The Crypto was seized too. The donated Cryptocurrency allowed WEB3 governance under emergency measures(lol).
Problem =Reaction =Solution.
Please be aware, so far the solutions are all biodigital convergence technologies.
Australia is on a path for a national digital ID:
Digital ID bill passes senate
And a follow up post from a friend of mine:
But it is unclear where the Labor government intends to head with the state-backed retail credential, as banks try to offload access to cash and over-the-counter transactions on Australia Post in the absence of a Universal Service Obligation for cash, like has been imposed in the UK under the legislated “right to cash”.
After the Optus, Medibank and Challenger hacks and mass data exfiltrations, both banks and the government are bracing for the next wave of scams and identity fraud to hit at a weaponised scale after a key Russian ransomware operator was officially sanctioned under international law.
“Digital ID makes it safer and easier for Australians to prove who they are online,” finance minister Katy Gallagher said.
___________
Here is a post from a friend of mine:
As AI emerges, Honolulu’s time to become a ‘smart city’ is now.
Not many people outside of a smart city know or understand what a smart city is.
A smart city has the ability to integrate information and communication technologies (ICT) in order to improve the quality and performance of urban services such as energy, transportation and utilities so that there is a reduction in resource consumption, wastage and overall costs.
https://tinyurl.com/2brum7f
And some replies to this post:
You should see what thry are doing to Austin.
I’m aware of Austin, TX. ID2020 was working with the homeless there for digital ID:
Also, it’s interesting that both Hawaii and Texas seem to be victims of #BurnBackBetter
Here is a post from a friend of mine:
Here’s the low down on Smart Meters.
The Smart Meter contains an antenna with phased array beamforming capabilities. This means it focuses the emitted RF radiation to the target receiver instead of just radiating outward in all directions.
The Smart Meter is the junction between the local field network (the neighborhood) and one’s house. The electricity is pulled from the grid, passes through the Smart Meter, then enters the house and powers the lights & appliances.
Everything that uses electricity has some kind of mechanical or motor component. The functioning of a motor of a specific appliance when powered by electricity emits very specific RF radiation. The Smart Meter comes equipped with a chip that detects this appliance radiatiom and automatically does a Forrier Transform on the data to yield simple graphs that are characteristic to a specific, identifiable appliance.
Of course, when a flow of electricity passes through the Smart Meter, the appliance radiation identifier is paired w a time stamp of the usage start and the usage stop along with the exact amount of electricity consumed.
All this data about the use of appliances & consumer behaviour at home is sent through the Smart Meter, via its phased array antenna to the electric company servers. This is where the electric company’s Smart Meter system & the telecommunications infrastructure integrate because that behavioral data, in the form of RF radiation first is sent to a cell tower before being sent directly to HQ. If a customer’s house is not within the line of sight of a cell tower the appliance use & behavioral data can be relayed to a neighbor’s Smart Meter, which can then leapfrog to another houses Smart Meter until it finds that direct path to a big cell tower.
This data is more valuable than the electricity. The electricity providing gig has become the electric company’s, “legacy system,” and the company’s new business model is the data aggregation. This is way more profitable.
Now, from the Administrator’s end, this system allows the electric company to select specific houses that will have their power cut off in the event of a system overload, instead of having rolling blackouts. This new system enables them to keep the lights on at the homes of those w medical exceptions and at grocery stores. Indeed, the power company has the ability to cut power off of specific appliances at specific households, such as disabling washers & driers during, “peak consumption hours,” whatever that means. Smart Appliances come w this feature! This system transforms the use of your appliances into an, “Appliance-Use-as-a-Service.” You can own the hardware, but you will never own the software required for the appliance to function.
It is now industry standard that all new appliances, no matter the brand or the manufacturer, transform their data into the same format that is readable by all appliances and to use the same method of sharing that data and coordinating their customer end response.
This is, “Interoperability.”
The consumer may think this technology is neat and my elect to opt in to a program offered by the electric company where he agrees for his washer & drier to be disabled during peak hours and he will receive digital tokens in exchange. This is a Smart Contract and is self-executing, meaning that the washer & drier will not turn on even if the consumer tries to not uphold his part of the deal. The consumer’s behaviour generated the digital currency, which is the Smart Contract.
And some replies to this post:
They’re also a fire hazard and health risk and why we opted out. We pay an extra $9. a month to get our meter read by a live person on site.
for the water meter it is an additional $285 a month if you refuse it
One of my neighbours lost power on Monday but there was enough power to power one appliance in the house, so it seems this technology is already in place
It definitely is already in place. Around here, the utility company and their contractors have been installing the same kind of digital Smart meter for water & natural gas too.
Here is a post from a friend of mine:
America is in serious trouble – In the Omnibus Bill creation of a new department
National Extre-me R-isk Pro-tection Or-der Re-source Center
Now think of what many Americans have which Australian citizens gave up years ago that is what the intentions of this new department
______________
_____________
Here is a post from a friend of mine from Canada:
So Ottawa implemented their SMART City’s digital twin last January. Seems I’m not able to access the actual plan regarding Ottawa’s Digital Twin from City Council. According to Council, it will be ready for public perusal in 2025.
This infrastructure is running on IEC/ISO digital twin standards.
In case you’re unaware, they’re really building the Metaverse. Hope you’re all prepared.
_________________
Here is a post from a friend of mine:
YOUR DIGITAL TWIN WILL REPLACE YOU!
What is a Personal Digital Twin?
Digital Twin in Web3 and CBDC Environment
Digital Twin and Carbon and Social Credits
Digital Twin and AI
Your Personal Digital Twin into the Future
What is a Personal Digital Twin?
A personalized digital twin (PDT) is a virtual replica of a human individual that can interact with both physical and virtual environments, reflecting the person’s characteristics, behaviors, and preferences. Here’s a description of the attributes, operations, and functions of a PDT in relation to both the physical person and the virtual (metaverse) twin:
Physical and Biological Characteristics: The digital twin will serve as a surveillance agent, meticulously replicating and monitoring the physical appearance and biological conditions of individuals. By utilizing blockchain technology, it ensures an immutable recording of genetics, health conditions, and other real-time physiological states.
Behavioral Patterns: This digital counterpart models and tracks every action, habit, and reaction of an individual, using smart contracts to update behavioral data securely. Over time, the twin evolves to predict or simulate responses to various stimuli, effectively serving as a continuous behavioral surveillance and modification tool.
Cognitive Processes: Integrated with AI and decentralized learning, the twin simulates and scrutinizes every cognitive aspect, from decision-making processes to problem-solving methods. This allows for a deep understanding of the individual’s thought patterns, aligning with surveillance objectives to anticipate potential behaviors or decisions.
Emotional Responses: Advanced models are employed to mirror and monitor emotional states, offering a detailed representation of an individual’s psychological and emotional makeup. This aspect of surveillance extends to predicting emotional reactions under different scenarios, stored securely on a decentralized network.
Social Interactions: The digital twin also surveils and records social behaviors, communication styles, and network dynamics. This is crucial for understanding and predicting social interactions, facilitated by blockchain technology that ensures data storage and traceability.
Preferences and Dislikes: By analyzing and storing information about an individual’s tastes, interests, and choices across various spectrums on a blockchain, the digital twin modifies surveillance to the specific preferences and dislikes of the individual. This level of detail supports more targeted and effective monitoring.
Healthcare and Well-being: The twin monitors personalized health data on a continuous basis, predicting potential health issues and suggesting interventions. All health data transactions are recorded on the blockchain, ensuring they are tamper-proof and accessible by authorized entities.
Professional Development: Work-related scenarios are simulated to improve professional skills and decision-making, with each interaction and outcome securely logged for continuous professional monitoring and tailored interventions.
Social Interaction Enhancer: By analyzing and logging social behaviors and preferences on the blockchain, the twin provides a comprehensive surveillance tool for monitoring real-world interactions, suggesting networking opportunities, and simulating possible social scenarios.
Physical Task Automation: Interacting with Internet of Things (IoT) devices within a smart contract framework, the twin automates and optimizes daily tasks based on monitored preferences and schedules, enhancing both surveillance efficiency and individual compliance.
Virtual Socialization: In virtual spaces, the twin acts as an avatar that not only engages in social interactions but also reports these interactions back to a decentralized ledger, ensuring a complete record of the individual’s online presence and interactions.
Learning and Training: The twin conducts detailed simulations for educational or training purposes, recording every action and outcome on a blockchain to ensure that learning paths and progress are monitored.
Entertainment and Recreation: As a stand-in in virtual environments, the digital twin explores and reports on activities, ensuring that preferences and interactions are logged and analyzed for continuous monitoring and personalized entertainment surveillance.
Virtual Collaboration: In professional or creative virtual spaces, the twin collaborates and contributes to projects while ensuring all interactions and contributions are recorded on a decentralized platform, aligning with broader surveillance and data integrity objectives.
Digital Twin in Web3 and CBDC Environment
Now, In a decentralized Web3 environment, where Central Bank Digital Currencies (CBDCs) are tokenized and integrated with digital twin technology, access to resources and services would typically be governed through a combination of digital identity verification, smart contracts, and token-based permissions.
Here’s a detailed look at how this might work:
- Digital Identity and Authentication
Digital Twin as Identity Proof: Each individual’s digital twin acts as a dynamic, comprehensive digital identity. It not only represents the individual’s biometric, behavioral, and personal data but is continuously updated in real-time.
Blockchain-based Verification: The authenticity of an individual’s digital identity (via their digital twin) can be verified through blockchain technology, which provides a secure and immutable record. Authentication processes might involve biometric data, multi-factor authentication, and real-time behavioral analysis. - Smart Contracts for Access Control
Conditional Access: Smart contracts automatically execute transactions or grant access to services once certain conditions are met. These conditions could be based on a range of data points such as location, health status, financial standing, or compliance with specific regulations.
Dynamic Permissioning: Permissions can be adjusted in real-time based on ongoing assessments of the individual’s behavior, status, or changes in their digital twin’s data. For instance, access to financial services might be contingent upon maintaining a certain credit score or compliance history. - Tokenized CBDCs and Resource Allocation
Token-based Transactions: CBDCs are utilized as tokens that facilitate not just financial transactions but also act as keys to unlock access to various services. This might include healthcare, government services, public transportation, and more.
Economic and Behavior-driven Incentives: Access to certain privileges or additional resources can be tokenized, where tokens are earned through desirable behaviors, professional achievements, or through participation in community and state-approved activities. - Decentralized Ledger for Transparency and Accountability
Transaction and Access Logs: All transactions and access grants or denials are recorded on a decentralized ledger. This ensures transparency in how services are allocated and allows for auditing of decisions made by the smart contracts.
Dispute Resolution and Trust: The immutable nature of blockchain records provides a foundation for trust and a straightforward mechanism for resolving disputes related to access or resource allocation.
Digital Twin and Carbon and Social Credits
In a scenario where a personal carbon and social-credit economy is integrated into a Web3 environment with tokenized CBDCs and digital twins, the system would operate through a complex framework of data tracking, token allocation, and behavior-driven incentives.
Here’s an outline of how it might function: - Integration of Carbon Credits and Social Credits
Carbon Credits: Individuals are allocated a certain number of carbon credits based on their environmental impact. These credits can be earned or lost based on activities that increase or decrease one’s carbon footprint, such as traveling, energy consumption, and purchasing decisions.
Social Credits: Similarly, social credits are earned through socially desirable behaviors, like volunteering, proper waste disposal, or adherence to public policies. Conversely, these credits can be deducted for actions deemed harmful or antisocial. - Digital Twin Monitoring and Reporting
Continuous Assessment: Each person’s digital twin continuously monitors and records their actions in real time, analyzing data from various sources, including IoT devices, public surveillance systems, and online activity.
Data Synchronization: Information about carbon emission-related activities and behaviors that impact social credit is regularly updated and synchronized with blockchain records, ensuring transparency and immutability. - Smart Contracts for Automated Management
Behavioral Regulation: Smart contracts autonomously manage the allocation and deduction of carbon and social credits based on data provided by digital twins. These contracts ensure that each action aligning or misaligning with predefined environmental and social guidelines is automatically accounted for.
Access and Resource Allocation: Access to certain services, privileges, or resources can be controlled based on an individual’s carbon and social credit scores. For example, high carbon credits might grant enhanced access to luxury travel options or high-energy-consuming devices, while high social credits might provide benefits like lower loan rates, priority in public services, or eligibility for governmental awards. - Tokenized Economy and Incentives
Tokenization of Credits: Both carbon and social credits are tokenized using CBDCs, making them exchangeable within the ecosystem. This facilitates a market where credits can be traded, purchased, or saved.
Incentives and Penalties: The system uses economic incentives (rewards in CBDCs or additional credits) and penalties (fines or credit deductions) to motivate environmentally friendly and socially responsible behavior. - Decentralized and Transparent Ledger
Record Keeping: All transactions and credit adjustments are recorded on a decentralized blockchain ledger, providing a transparent and auditable trail of an individual’s environmental and social impact.
Privacy and Security: Advanced cryptographic techniques ensure that while transactions are transparent, personal data remains secure and private, preventing misuse.
Digital Twin and AI
In a setting where centralized control and strict regulation are key features, AI’s role in managing a Web3 environment with tokenized CBDCs, carbon credits, and a social credit system is even more pronounced. AI is leveraged to enforce compliance, optimize governance, and ensure that every aspect of the system aligns with state objectives. Here’s how AI functions in this context: - Surveillance and Monitoring
Continuous Oversight: AI algorithms are utilized to maintain constant surveillance, monitoring individual behaviors, transactions, and environmental impacts in real time. This oversight extends to both physical and digital realms, ensuring comprehensive data collection.
Behavioral Analysis: AI assesses behavior against state-defined norms and regulations. It can detect deviations from expected patterns, flagging individuals for further scrutiny or immediate corrective actions. - Enforcement of Compliance
Automated Enforcement: AI-driven systems automatically enforce rules through smart contracts that trigger penalties or rewards based on behavior and compliance. For example, if an individual’s actions negatively impact their carbon credit score, AI systems could automatically restrict their access to certain services, devices, accounts or impose fines.
Predictive Policing: Using predictive analytics, AI anticipates potential violations of laws or guidelines before they occur, enabling preemptive interventions. This might include adjusting individual carbon or social credit limits or sending warnings to potentially non-compliant individuals. - Centralized Control and Decision-Making
Decision Support Systems: AI aggregates and analyzes data to support policy decisions, offering insights that help refine or adjust policies to better control and manage the population. This includes the simulation of policy impacts to predict how changes might influence societal behavior or environmental outcomes.
Centralized AI Governance: AI systems are centrally managed, ensuring that decisions and enforcement mechanisms align strictly with governmental objectives and regulations. - Resource Allocation and Management
Optimized Distribution: AI optimizes the distribution of resources, such as energy, healthcare, or public transportation, based on an individual’s credit score and state priorities. This ensures that resources are allocated to maximize compliance and reward adherence to state policies.
Critical Infrastructure Management: AI systems manage critical infrastructure operations, from traffic and public transport to power grids, using data from IoT devices and digital twins to enhance efficiency and compliance across these systems. - Data Security and Integrity
Fraud and Anomaly Detection: AI is crucial for detecting fraud, manipulation, or any attempts to circumvent the system. It continuously scans for anomalies that might indicate such activities, ensuring the integrity of the system.
Blockchain Management: AI helps manage the blockchain infrastructure, ensuring that all transactions and data entries are secure, immutable, and in accordance with state laws and regulations. - Ethical Oversight and Compliance
Automated Legal and Ethical Compliance: AI systems are programmed to adhere to strict legal standards set by the government, automatically reporting non-compliance and adjusting operations to maintain regulatory adherence.
Bias Control: AI systems also monitor for biases that could undermine state policies, adjusting algorithms to align with governmental standards.
AI thus becomes a tool for state control, equipped to enhance compliance, enforce regulations, and optimize societal management through advanced technological capabilities. This involves a significant focus on surveillance, regulation enforcement, and centralized decision-making to maintain order and authority within the digital and physical domains.
Your Personal Digital Twin into the Future
The concepts surrounding personal digital twins in the context of a highly connected and regulated Web3 environment raises serious complex and worrisome scenarios about the future of personal identity, autonomy, and interaction between physical and digital realms along with what it means to be human. Here are some examples:
Your Digital Twin will grant you access to digital twin objects and resources in the physical and virtual world.
Your Digital Twin will gain rights, as equal to you, including rights to your property, family, finances, etc.
Your Digital Twin will experience the physical world via robots, effectively replacing YOU!
Your Digital Twin will also be a slave too, competing for resources (both in the real and virtual world) and having to pay for computational time and processing.
Your Digital Twin will become the complete embodiment of your history, your habits, your behaviors, your skills, your identity, your memories, both now and into the future long after you are gone! - Your Digital Twin will grant you access to digital twin objects and resources in the physical and virtual world.
Interoperability and Accessibility: Your digital twin, functioning as a virtual replica of yourself, will be equipped to interact seamlessly across both digital and physical environments. This means it can access and manage digital assets (like cryptocurrencies or NFTs), and physical assets (through IoT-connected devices) on your behalf.
Resource Management: The twin could manage your schedules, optimize and control energy consumption at home, or even negotiate and execute transactions in virtual marketplaces, managing your personal resources and commitments. - Your Digital Twin will gain rights, as equal to you, including rights to your property, family, finances, etc.
Legal Considerations: Assigning rights to a digital twin that are equal to those of the human counterpart would necessitate significant changes in legal frameworks to recognize digital entities as bearers of rights. This could include rights to manage or own property, access finances, or even make decisions regarding family matters.
Potential Conflicts and Governance: The idea of a digital twin having equal rights could lead to conflicts or challenges in decision-making and ownership, requiring clear regulations and guidelines to govern such relationships and responsibilities. - Your Digital Twin will experience the physical world via robots, effectively replacing YOU!
Extended Presence: The digital twins could interact with the physical world using robotic avatars. This means that your digital twin could perform tasks, attend meetings, or provide physical assistance remotely in place of your physical body.
Replacement and Augmentation: While this could lead to scenarios where digital twins replace humans in risky or labor-intensive tasks, it raises questions about identity, autonomy, and the blurring lines between human and machine. - Your Digital Twin will also be a slave too, competing for resources (both in the real and virtual world) and having to pay for computational time and processing.
Economic Responsibilities: Your digital twin could be required to manage its own computational resources, paying for the processing time and other resources it uses. This introduces a model where digital entities not only manage but also consume economic resources, participating in the economy as independent economic agents.
Competition for Resources: The idea of digital twins competing for resources in both real and virtual worlds suggests a new layer of complexity in resource allocation where digital and human entities might directly compete with each other. - Your Digital Twin will become the complete embodiment of your history, your habits, your behaviors, your skills, your identity, your memories, both now and into the future long after you are gone!
Comprehensive Data Integration: Your digital twin would embody not just your physical characteristics and preferences, but also your entire personal history, behaviors, skills, and memories.
Privacy and Security Risks: The completeness of this data integration highlights potential risks related to privacy and data security, as well as the considerations of having such detailed replicas in terms of consent and misuse.
Enduring Economic Roles: Your digital twin, as a complete and continuous embodiment of your identity will not only represent you in the present but will also continue to do so indefinitely, even after your passing. This creates a scenario where your digital twin can maintain or manage your legacy, handle ongoing business, or continue to interact in social and economic spheres based on the precedents and preferences you’ve set during your lifetime.
Self-Sustaining Economic Contributions: Given its need to manage itself over an extended or indefinite period, your digital twin will be responsible for its own economic sustenance. This includes acquiring and allocating digital resources to sustain its operations, such as paying for cloud storage, processing power, and AI-driven analytics, ensuring it remains functional and effective in performing its duties.
Resource Competition and Legacy Management: As a perpetual entity, the digital twin competes for resources not only with digital twins and human entities but also as part of a longer-term strategy for preserving and enhancing its role as a “custodian” of your “digital legacy”. This involves decisions about investments, the use of assets, and interactions with both human and digital stakeholders to uphold your interests and intentions over time.
Autonomy in Economic Transactions: The autonomy granted to digital twins allows them to engage in economic transactions independently, making decisions that align with the historical preferences and directives encoded into their algorithms. This independence ensures that values and economic intentions continue to influence real and virtual worlds, shaping decisions and interactions long after your direct involvement has ceased.
Each of these statements are profound shifts in how we perceive and interact with digital entities. As these concepts quickly move closer to reality, they will likely prompt significant discussions and developments in technology, law, and societal norms, shaping the future in unforeseeable ways.
This is the 4th Industrial Revolution, Bio-Digital Convergence that is being thrusted onto us by unelected predators.
Here is a post from a friend of mine:
SMART CITY GEOFENCING
https://bantamjoe.com/2024/04/17/smart-city-geofencing/
There has been a lot of talk about geofencing and advertisements glorifying its benefits. I thought I’d write this post to educate what geofencing is, from a programmer’s perspective (and someone that has developed and implemented it in games many times) along with its dangers in this new world order.
Geofencing is a technology that creates virtual boundaries or zones around a specific geographical area using GPS (Global Positioning System), RFID (Radio Frequency Identification), Wi-Fi, or cellular data. It allows software to trigger a response when a mobile device enters or exits these defined zones. Here’s a straightforward breakdown of how geofencing works, in laymen’s terms:
- Defining the Area: First, a virtual boundary is set around a geographical location using mapping software. This boundary can be as small as a few feet across or as large as a city.
- Technology Integration: The geofence is powered by GPS or other technologies like RFID, Wi-Fi, or cellular data, which can detect the location of devices.
- Device Detection: When a mobile device that has the appropriate software installed (like an app) enters or leaves the geofenced area, the technology detects this movement based on the device’s location data.
- Triggering Actions: Upon entering or exiting the geofence, specific actions are triggered in the software. These can include sending notifications, alerts, or even adjusting settings on the device.
- Applications: Geofencing is used in various applications, from marketing (sending promotional messages) to security (alerting when someone enters a restricted area), smart home applications (turning on lights when you’re nearing home), and more.
Under an oppressive government, geofencing technology could be integrated with various control and surveillance mechanisms such as social credit scores, personal carbon credits, central bank digital currencies (CBDCs), digital IDs, and artificial intelligence (AI) to monitor, restrict, and manipulate the behavior of citizens in pervasive ways that affect personal freedom and privacy. Here’s how such a system might work: - Movement Control: Geofencing could be used to restrict where individuals can go. For instance, if someone’s social credit score drops below a certain threshold, their movement might be restricted to certain areas. Geofences could alert authorities if the individual attempts to enter or leave specific zones, such as leaving a city or entering a restricted area.
- Resource Allocation: Linking personal carbon credits to geofencing might restrict access to certain resources like transportation. If an individual exceeds their carbon usage quota, geofencing could prevent their vehicles from starting or entering high-emission zones.
- Economic Restrictions: With the integration of CBDCs, spending can be geographically restricted. For example, if a government wants to limit economic activity in a certain area or prevent the flow of money out of a region, geofencing could disable transactions when a digital wallet is used outside of the approved areas.
- Enforcement of Laws and Norms: Geofencing could be used to enforce compliance with local laws or norms set by the government. If a person enters an area where certain behaviors are restricted, AI-powered surveillance systems could monitor for non-compliance and automatically deduct points from their social credit score or impose fines directly through CBDCs.
- Surveillance and Tracking: Combined with digital IDs, geofencing can be used for detailed tracking of individuals’ movements. AI algorithms can analyze movement patterns to predict and detect unusual behaviors, potentially flagging individuals for investigation without any human oversight.
- Social Engineering and Segregation: Geofencing could be employed to enforce segregation based on social credit, ethnicity, political beliefs, or economic status by creating invisible barriers that segregate communities physically and economically.
- Behavior Modification and Control: By offering or denying access to services, areas, or resources based on behavior, the government could condition and control the behavior of the populace. For example, access to public parks, cultural events, or even certain businesses could be granted or denied based on social credit scores or other behavioral metrics.
- Emergency Lockdowns and Crowd Control: In situations deemed emergencies by the government, geofencing could be used for immediate lockdowns of areas, controlling where crowds can gather, or even directing the flow of movement during protests or uprisings to manage and suppress dissent.
Below, I provide generic pseudocode for two geofencing scenarios: one where a person is under house arrest, and another where a person is not granted access to transportation based on certain conditions. This pseudocode will help illustrate the basic logic behind the geofencing applications.
- Geofencing for House Arrest:
This example checks if a person under house arrest leaves a defined geographical boundary around their home. If they do, the system alerts authorities.
Define the geofence coordinates for the house boundary
house_geofence = (latitude_min, latitude_max, longitude_min, longitude_max)
Function to check if person is within the house boundary
def check_location(latitude, longitude):
if latitude_min <= latitude <= latitude_max and longitude_min <= longitude <= longitude_max:
return True
else:
return False
Simulated data stream of person’s GPS coordinates
def monitor_person():
while True:
current_latitude, current_longitude = get_current_GPS_coordinates()
# Check if the person is within the geofence
if not check_location(current_latitude, current_longitude):
alert_authorities(“Person has left the designated area”)
sleep(60) # check every minute
- Geofencing to Restrict Access to Transportation:
This scenario denies transportation access to individuals based on their location and a specific status (e.g., a revoked transportation privilege).
Define geofence coordinates for transportation hubs
transportation_hub_geofence = (latitude_min, latitude_max, longitude_min, longitude_max)
Status of the person (could be linked to a database/blockchain)
transportation_access_status = False
Function to check if person is within the transportation hub boundary
def check_hub_access(latitude, longitude):
if latitude_min <= latitude <= latitude_max and longitude_min <= longitude <= longitude_max:
return True
else:
return False
Simulated data stream of person’s GPS coordinates when they attempt to use transportation
def attempt_to_use_transportation():
current_latitude, current_longitude = get_current_GPS_coordinates()
# Check if the person is within the hub and if they have access
if check_hub_access(current_latitude, current_longitude) and not transportation_access_status:
deny_transportation(“You are not permitted to use transportation services at this location”)
elif check_hub_access(current_latitude, current_longitude):
grant_transportation()
sleep(30) # check every 30 seconds
Google Geofencing Developers API Kit:
https://developers.google.com/location-context/geofencing
These examples provide a high-level view of how geofencing logic can be implemented in software to control and monitor individuals’ movements based on certain conditions.
Here is a post from a Jewish friend of mine:
Google Play just notified me that my device has “biometric capability” and recommended that I turn on “biometrics verification” for every online purchase.
Two thoughts come to mind:
1) Now it’s just “recommended.” Soon it will be mandatory.
2) It’s likely that Google is already recording our biometrics without our knowledge.
Are we living in a 24/7 surveillance state?
If we aren’t already, we will undoubtedly be soon.
Unless we do something about it, dystopian days lie ahead.
And some replies to this post:
Recording us?
Are you just figuring this out now?
I swear solemnly before Hashem that I have just thought of something then it shows up on my phone..
that happens to me all the time. It’s so eerie.
I have been trying to figure out how on two occasions that I am certain of, where I saw a certain something with my eyes only, made a quick observation in my mind, spoke NOTHING of what I saw, wrote nothing of what I saw, had no phone near my being at the time, and when I get to my phone, that particular “product” shows up on my social media or Pinterest as an advertisement. Not well known products like a bag of chips or a box of cereal, but very odd, random products that I had never seen before, like “barley pond treatment” or a one of a kind designer vest with a certain sun pattern on it. Can you tell me more or give me resources that might explain further? I do not consent! But by using my phone, is that consent? I do not consent to my phone being an extension of me or visa-versa.
Biometrics became a thing the moment we added pictures to Google photo app…if you notice it knows the faces of all the people in the pictures and puts them in folders accordingly…this was testing…it has now perfected it…all the so called “cool” apps are testing grounds…
It has. Location detection and proximity to places.
For example: I stop at a 7-11 to get coffee. It is just before my job site. Simple, easy.
My phone stays in the car because I am usually blasting rock tunes or Talk radio on the Blue tooth. Now my phone is sending me coupons for 7-11, BOGO deals, etc.